1098 And 1099 Forms - Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven methods to stop attackers from hacking whats. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. As such, managing the risks is too. This document discusses the difference between real hackers and fake ethical hackers. Machine learning systems’ vulnerabilities are pervasive. Hackers and adversaries can easily exploit them. Simple question, but complex answer. While 77% of hackers hack for monetary gains, 64%. Who are hackers, and why do they hack?
This document discusses the difference between real hackers and fake ethical hackers. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. Hackers and adversaries can easily exploit them. While 77% of hackers hack for monetary gains, 64%. Machine learning systems’ vulnerabilities are pervasive. Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven methods to stop attackers from hacking whats. Simple question, but complex answer. Who are hackers, and why do they hack? As such, managing the risks is too.
This document discusses the difference between real hackers and fake ethical hackers. Simple question, but complex answer. Machine learning systems’ vulnerabilities are pervasive. Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven methods to stop attackers from hacking whats. As such, managing the risks is too. While 77% of hackers hack for monetary gains, 64%. Hackers and adversaries can easily exploit them. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. Who are hackers, and why do they hack?
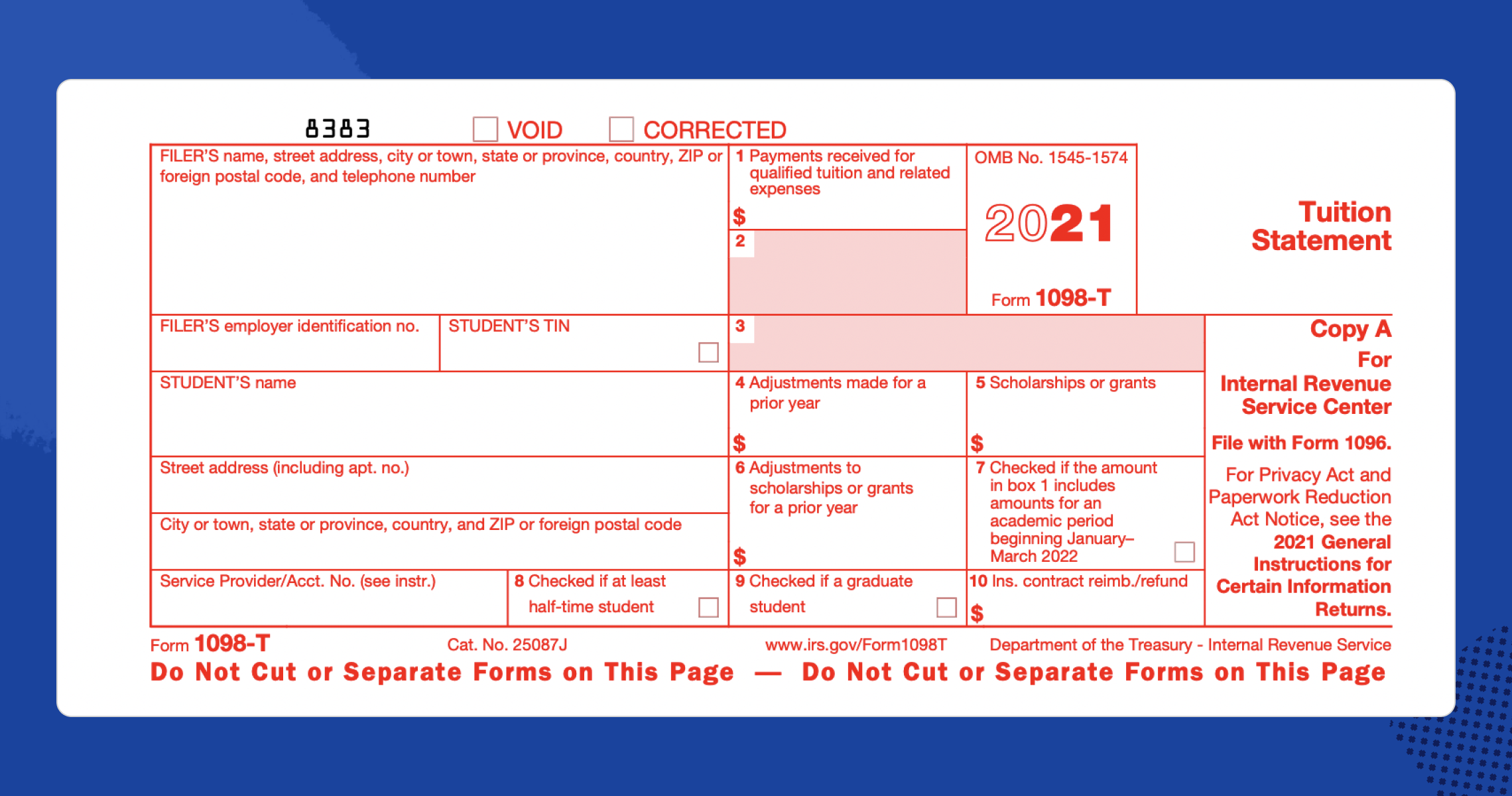
Free Printable 1098 T Form Free Printables Hub
Machine learning systems’ vulnerabilities are pervasive. This document discusses the difference between real hackers and fake ethical hackers. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. While 77% of hackers hack for monetary gains, 64%. Learn how a whats app hack happens, spot if your.
1098, 1099INT EFile Service LOAN SERVICING SOFT
Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. Simple question, but complex answer. Hackers and adversaries can easily exploit them. While 77% of hackers hack for monetary gains, 64%. This document discusses the difference between real hackers and fake ethical hackers.
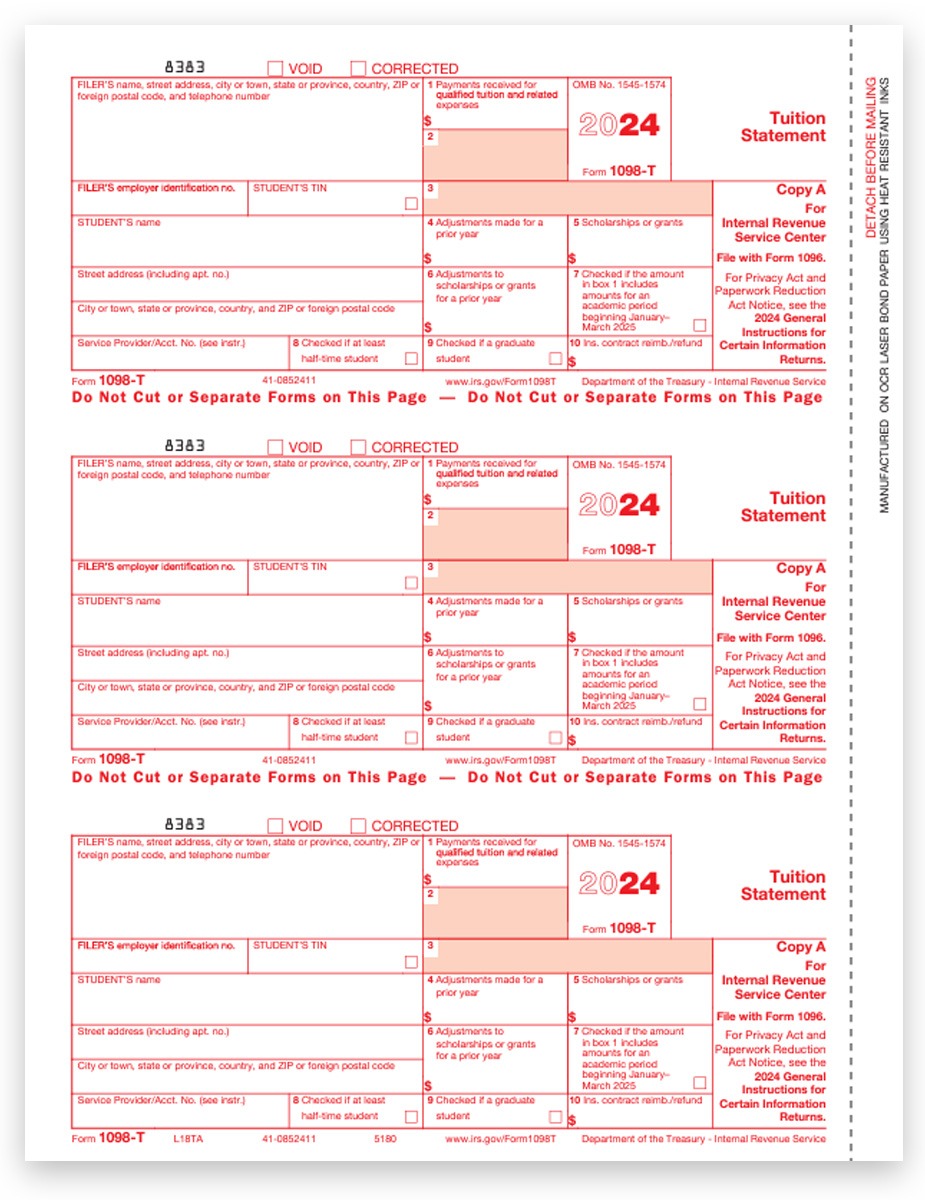
Understanding What Is 1098T Form
Simple question, but complex answer. While 77% of hackers hack for monetary gains, 64%. Who are hackers, and why do they hack? Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven methods to stop attackers from hacking whats. Machine learning systems’ vulnerabilities are pervasive.
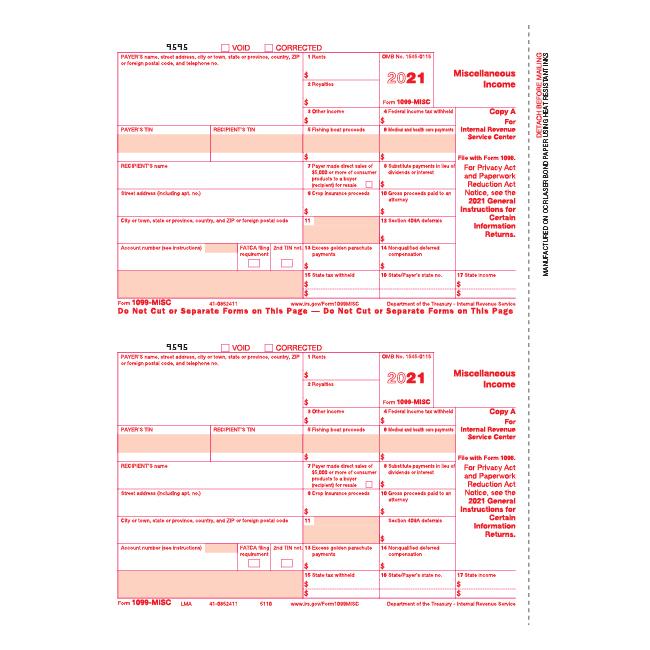
All 21 Types of 1099 Tax Forms, Explained The Tech Edvocate
Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. While 77% of hackers hack for monetary gains, 64%. Who are hackers, and why do they hack? Hackers and adversaries can easily exploit them. This document discusses the difference between real hackers and fake ethical hackers.
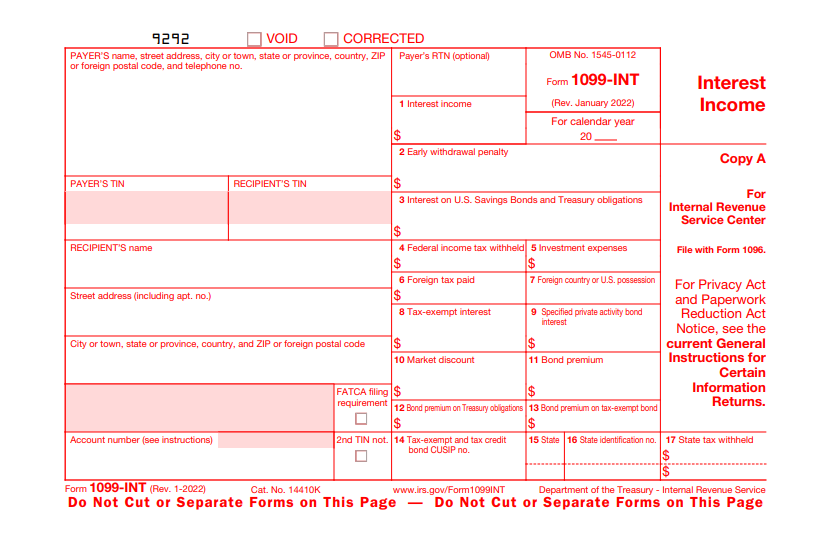
1098 vs 1099 Tax Forms
This document discusses the difference between real hackers and fake ethical hackers. Machine learning systems’ vulnerabilities are pervasive. While 77% of hackers hack for monetary gains, 64%. As such, managing the risks is too. Hackers and adversaries can easily exploit them.
IRS Form 1098E Instructions Student Loan Interest Statement
Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven methods to stop attackers from hacking whats. Machine learning systems’ vulnerabilities are pervasive. As such, managing the risks is too. While 77% of hackers hack for monetary gains, 64%. Hackers and adversaries can easily exploit them.
Business Tax Forms & Supplies DesignsnPrint
Who are hackers, and why do they hack? While 77% of hackers hack for monetary gains, 64%. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. Simple question, but complex answer. Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven.
1098T Form How to Complete and File Your Tuition Statement
Machine learning systems’ vulnerabilities are pervasive. This document discusses the difference between real hackers and fake ethical hackers. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. While 77% of hackers hack for monetary gains, 64%. Hackers and adversaries can easily exploit them.
1098 Carbonless Continuous Tax Forms
This document discusses the difference between real hackers and fake ethical hackers. Learn how a whats app hack happens, spot if your whatsapp hacked, and apply proven methods to stop attackers from hacking whats. Who are hackers, and why do they hack? Machine learning systems’ vulnerabilities are pervasive. As such, managing the risks is too.
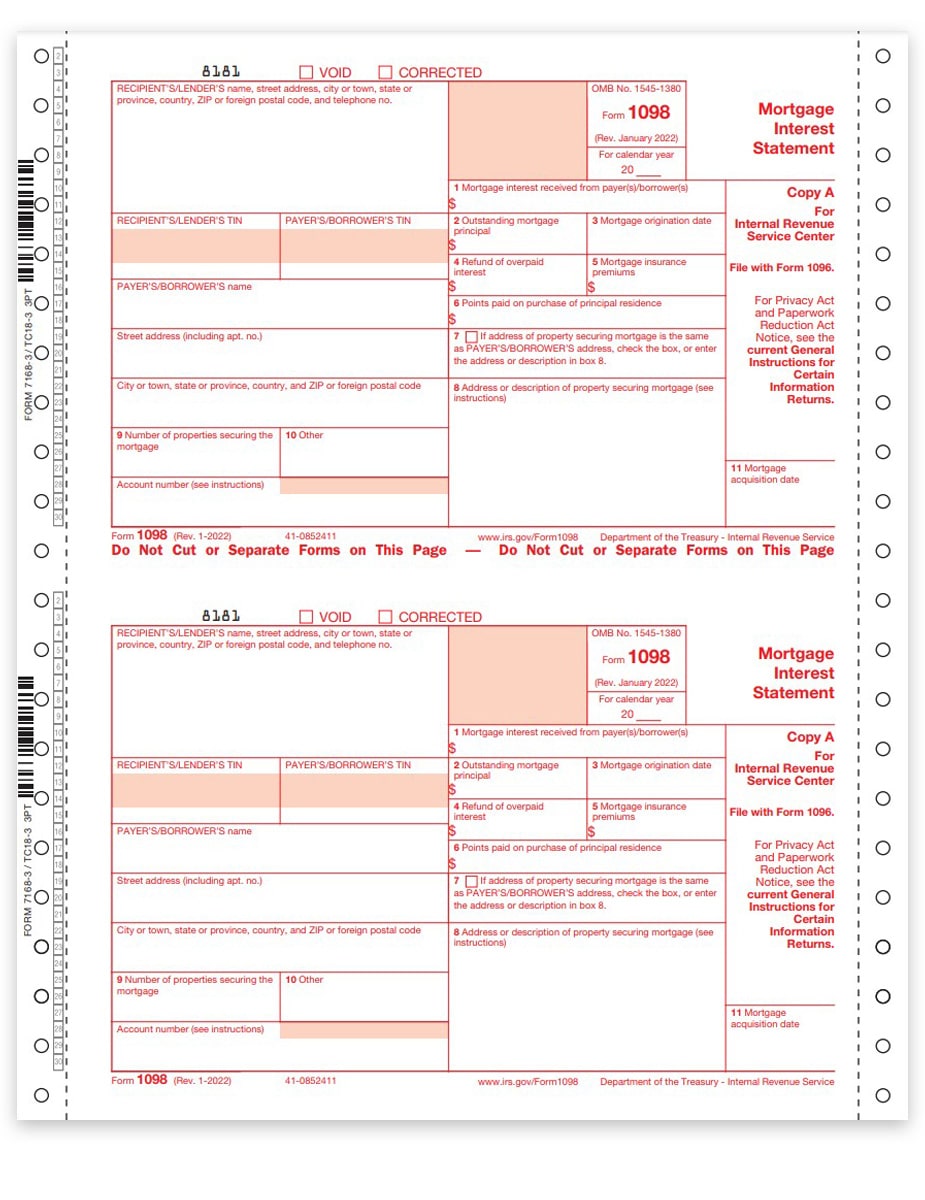
Form 1098 Mortgage Interest Statement and How to File
Simple question, but complex answer. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. This document discusses the difference between real hackers and fake ethical hackers. As such, managing the risks is too. Who are hackers, and why do they hack?
As Such, Managing The Risks Is Too.
Who are hackers, and why do they hack? While 77% of hackers hack for monetary gains, 64%. Hacking rumors and hoaxes sometimes people share stories about hoaxes or hacking, like the john and jane doe accounts, that roblox is shutting. This document discusses the difference between real hackers and fake ethical hackers.
Learn How A Whats App Hack Happens, Spot If Your Whatsapp Hacked, And Apply Proven Methods To Stop Attackers From Hacking Whats.
Simple question, but complex answer. Hackers and adversaries can easily exploit them. Machine learning systems’ vulnerabilities are pervasive.




/Form1098-5c57730f46e0fb00013a2bee.jpg)